 Safeguarding customer data while delivering omnichannel experiences is a choreographed dance between an enterprise and marketing cloud vendors. With GDPR, CCPA, and other state data privacy laws cropping up, and with consumers demanding real-time, personalized experiences that are consistent across channels, the delicate push-and-pull is now under a glaring spotlight.
Safeguarding customer data while delivering omnichannel experiences is a choreographed dance between an enterprise and marketing cloud vendors. With GDPR, CCPA, and other state data privacy laws cropping up, and with consumers demanding real-time, personalized experiences that are consistent across channels, the delicate push-and-pull is now under a glaring spotlight.
It’s a challenging time. An enterprise must be compliant, yet still provide customers a personalized customer experience that has been shown to drive revenue. Consider, for example, a recent Merkle study where 66 percent of consumers rated experience over price when making a purchasing decision.
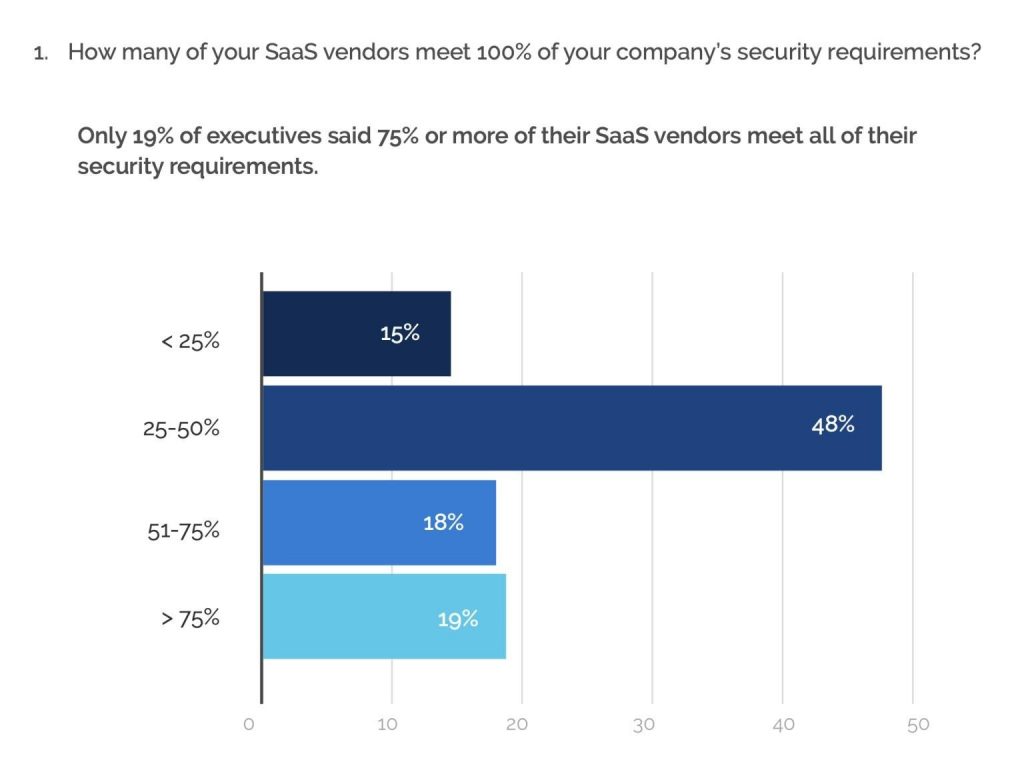
A recent study by Scott Brinker shows a scant 19 percent of executives believed that their cloud providers were even 75 percent compliant with their security practices. With increasing scrutiny and penalties for violations and the unspoken premise for SaaS (bypass your internal IT), it’s a real question whether SaaS models are even viable in the enterprise unless they seriously up their security game.
How to strike the right balance brings the issue of the cloud security perimeter surrounding data to the forefront. When an enterprise moves its customer data to a vendor’s cloud solution, it puts its faith in that vendor’s security perimeter.
With tightening privacy regulations, potential risks to reputation and capital are so great that companies are increasingly reluctant to make this trade-off, barring full indemnification – a non-starter for any SaaS vendor. In addition, omnichannel customer engagement requires the ingestion of customer data from multiple sources and channels. A typical cloud environment with multiple SaaS applications introduces risk by requiring that data move between applications, and between the client and vendor.
Decisions on how to balance data privacy with functionality differ for every company based on size and industry, but the answer for large-scale enterprises is to own the cloud security perimeter. Particularly for enterprises with a strategic imperative to provide a personalized customer experience, this ensures visibility and control over all data that sits inside the perimeter.
A previous blog in this space examined the Redpoint cloud advantage, a hybrid cloud solution that can sit inside of a company’s security perimeter. The deployment model preserves the control and integration needed to provide a hyper-personalized customer experience that drives revenue while mitigating risk and providing enterprise-grade security.
Being able to control customer data inside your own security perimeter provides enormous advantages beyond security, especially pertaining to providing a differentiated customer experience.
Control at a Granular Level
The benefit of keeping all customer data “under one roof” is immeasurable, but it’s also important to have controls in place to ensure proper data management. In a crowded customer data platform (CDP) market, not every vendor can claim a data layer that does more than ingesting data from multiple sources. While most every CDP will have data flowing from external websites, internal enterprise sites, and third-party sites, there are many data requirements that direct the appropriate connections for the ingested data. Tasks such as data encryption, encryption in transit, multi-factor authentication, and audit measures ensure that data permissions are met.
While the fulfillment of these data requirements are common for enterprise software outside of the marketing purview, the functionality is all too often missing for a CDP that sits in a public cloud. CDPs with advanced data management provides unmatched flexibility while policing data management guidelines to satisfy various requirements.
A CDP with this functionality that sits inside the cloud security perimeter is unfettered by the typical restrictions that surface when customer data must cross boundaries between various applications. Data integration is simplified, it is accessible to those applications that need it (and accessible in real-time), and there is only one set of data security measures that the enterprise fully controls. The secure environment allows for a consistent, holistic approach to data privacy and compliance, while also giving marketers the flexibility needed to create innovative and differentiated customer experiences.
Best of All Worlds
The only catch for this type of environment – if it can be called that – is the business is going to have to collaborate with IT, which runs counter to the SaaS argument that the IT function can be outsourced along with data management. Deploying software within an enterprise’s private cloud gets the best of all worlds: marketers are empowered to market creatively, IT is empowered to protect the enterprise’s data assets, and the enterprise can take advantage of new innovations from a CDP software vendor.
Another important point is that when an enterprise entrusts customer data to an external vendor, it usually must sacrifice records that would likely be useful if kept in a CDP within the security perimeter. A SaaS, in other words, will for the most part only handle short data records for channels and applications such as email, CRM, and other marketing records. A true, complete 360-degree customer view, however, is only possible by ingesting customer data from any source and retaining even the smallest detailed data for that customer’s lifetime.
Safeguarding data privacy and providing a personalized customer experience are too important for enterprise companies to entrust their data to an external vendor. With an enterprise-grade CDP that sits inside its own security perimeter, an enterprise has the best of both worlds: enterprise-grade security and a mission-critical solution that gives marketers complete access and control over customer data to drive revenue growth.
RELATED CONTENT
The Cloud Advantage: Control Your Own Security Perimeter
Why the Right to Be Forgotten is One of the Hardest Parts of GDPR
No Data Left Behind: Analytics, Orchestration, and Making Data Work for You


